1. Acronis Active Protection
Pattern detection
Observes patterns in how data files are being changed on a system. One set of behaviours may be typical and expected.
Another set of behaviours may signal a suspect process taking hostile action against files. The Acronis approach looks at these actions and compares them to malicious behaviour patterns.

Whitelist and Blacklist
Detect new threats based on already identified patterns as well as learned ones. Results must be adjusted to reduce false positive detection of things that really are not ransomware.
Maintains a whitelist — programmes that are allowed and expected to perform certain actions — to prevent authorised activities from being falsely tagged as unauthorised

Self-defense of backup files
Implemented a robust self-defense mechanism that will not let criminals disrupt the work of the Acronis application or backup file content.
Monitors the Master Boot Record of Windows-based computers. It will not let any illegitimate changes to be made to prevent you from being able to properly boot your computer.
How Acronis recovers files?
If ransomware begins to encrypt files, Acronis quickly detects and halts this process.
On any data that was exposed and encrypted before the process was halted can be recovered from a variety of backup sources.
2. Acronis AnyData Engine

Acronis data protection solutions powered by the AnyData Engine are lean, modular, secure and scalable. Image-based backups quickly capture and store all data in a universal backup format allowing recovery to any hardware or virtual machine.
The advanced policy engine ensures secure access and compliance. With the Acronis AnyData Engine, buy only what you need, get everything you want, and easily evolve with your business.
The advanced policy engine ensures secure access and compliance. With the Acronis AnyData Engine, buy only what you need, get everything you want, and easily evolve with your business.
Complete and Flexible New Generation Data Protection
Capture, store, recover, control and access data in virtual, physical, cloud and mobile environments.
- Any Protection: Data Backup, Bare Metal Restore, Migration, System Deployment
- Any Devices: Servers and Workstations
- Any Servers: Physical and Virtual
- Any OS Environments: Windows and Linux
- Any File System: NTFS, ReFS, FAT16/32, Ext2/3/4, ReiserFS3, XFS, JFS and more
- Any Virtual Environments: VMware, Hyper-V, XenServer, RHEV, Linux KVM, and Oracle VM
- Any Migration: V2V, V2P, P2V, P2P
- Any Applications: MS Exchange, MS SQL Server, SharePoint, Active Directory
- Any Storage Locations: Cloud, including Acronis Cloud; On-Premise and Remote Offices
3. Acronis Notary
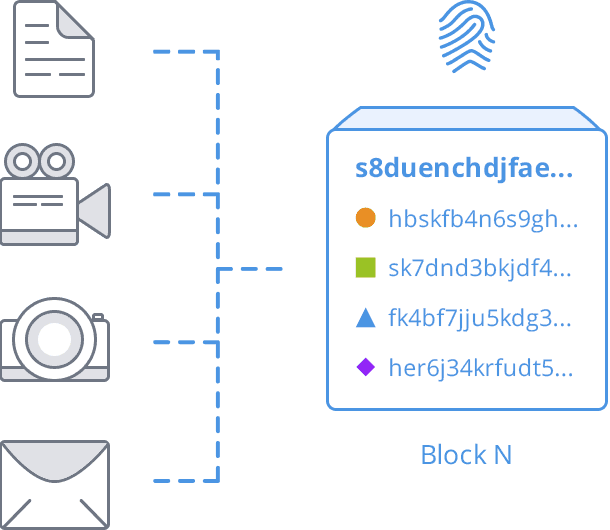
Blockchain
Famous in the context of the digital currency called bitcoin.
Acronis is the first consumer backup product to use Blockchain technology to prove a file is authentic and unchanged since it was backed up.
It distributes database that maintains a continuous growing list, or chain of data transaction records. Every portion of this decentralised system has a copy of the chain of records; no “official” copy exists. In this way, the information is secure from tampering and revision.
It distributes database that maintains a continuous growing list, or chain of data transaction records. Every portion of this decentralised system has a copy of the chain of records; no “official” copy exists. In this way, the information is secure from tampering and revision.
Data “Fingerprints”
Acronis Notary computes a cryptographic “fingerprint” hash of each file that is unique for each file. This hash algorithm produces the same output given the exact same input file every time, regardless of circumstance
What Notary does ?
When you back up your data to local drives or the cloud, you correctly expect your backup solution to faithfully back up those files. Acronis Notary technology can add a level of confidence to the authenticity of your data.
Acronis Notary creates a certificate for each notarised file. This certificate connects the unique file features with the permanent record in the blockchain. This allows you to check its authenticity.
Acronis Notary creates a certificate for each notarised file. This certificate connects the unique file features with the permanent record in the blockchain. This allows you to check its authenticity.
4. Acronis ASign
With Acronis ASign, your customers can digitally capture the electronic signature of one or more people on a backed-up document and generate unique certificates that contain images of the signatures, time stamps, and other information.
Acronis ASign Reduce miscommunication with users, suppliers, and customers, supporting the authenticity of your files with signatures enabled by blockchain.
The certificates are an audit trail that can be verified as authentic using blockchain technology.
The certificates are an audit trail that can be verified as authentic using blockchain technology.


Aconis
Backup Cloud Solution
World Fastest Backup & Recovery Sofware Solution
Complete Solution for Backup & Disaster Recovery
World Fastest Backup & Recovery Sofware Solution
Complete Solution for Backup & Disaster Recovery